Defence-In-Depth Cloud Security. Because part of a solution is no solution at all.
In an era of mandatory breach reporting, cloud security challenges are growing. But budgets are not. The answer for many is to sweat their assets in Colocation Data Centres to free time, money and talent for wider Hybrid and Private Cloud opportunities. If this is your preferred approach, you’re in good company. 9 in 10 Australian organisations have, or plan to have, a multi-cloud solution1. But the distributed design that makes Cloud computing so compelling can also be it’s Achilles’ heel.
Whether you’re being specifically targeted, or just probed for vulnerabilities, you need solutions in place against external threats. That’s where we come in. No one provider does it all, and certainly not best of all. And today, perimeter security is no longer enough. It means a complete, defence-in-depth security model must be applied. Because it’s about the technology. And the people.
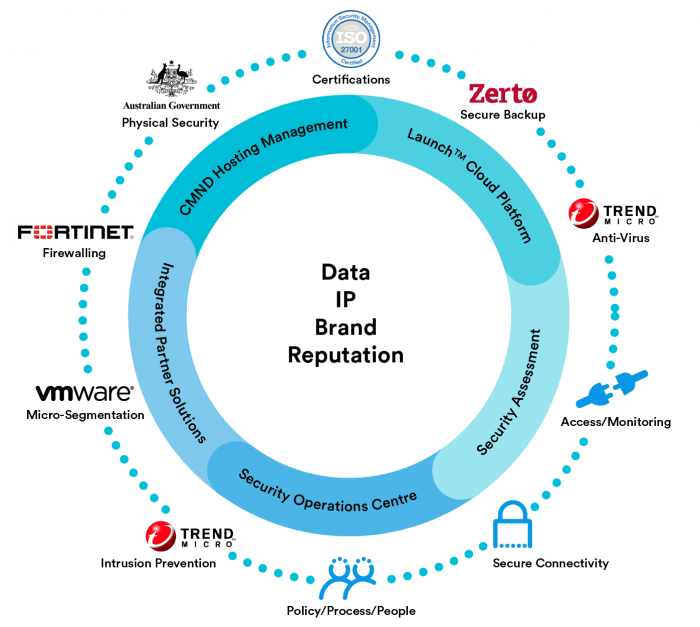
As Australia’s leading provider of Government Cloud services, VMware’s exclusive Australian Showcase Partner and a member of the Australian Cyber Security Council we are uniquely placed to deliver a complete 10-point security model to protect you today. And tomorrow.
- Physical security It all starts with controlling who has access to critical infrastructure, how, when and with what controls and logging. This has always been true for your team. But it must be true for your providers team as well.
- Tiered Security requirements. Cost-effective solutions consider the different needs of different data, workloads and apps.
- Anti-Virus (AV) e.g. Trend Micro Deep Security TM)). Your AV platform needs to deliver on its security promises but must also deeply integrate with management, patching, monitoring and logging tools to simplify and strengthen your environment.
- Intrusion Identifications & Prevention (HIPS). These technologies answer the question – have you already been breached? Are you being probed? What actions are required to prevent intrusion? Your obligations under mandatory breach reporting legislation make this indispensable for cloud security.
- Firewalling. Your provider must be able to deliver your reference design – or theirs – with the combination of virtual or physical appliances tailored to your specific requirements. Simple management is vital for what can be a low-return, and time-consuming area for your team.
- Micro-segmentation (e.g. VMware NSXTM). Traditional security models present a strong perimeter but mean the penetration of any low-security system puts everything at risk. Micro-segmentation puts a virtual firewall around every Virtual Machine (VM) to protect east-west traffic inside your data centre.
- Secure connectivity (e.g. Secure Internet Gateways). Some sectors demand Secure Internet Gateways and PROTECTED SCEC assessments, but every user must ensure data is protected both at rest and in flight, because any system is only as strong as its weakest link. Because we’re a leading carrier-neutral business-facing Telco in our own right we’re uniquely placed to cost-effectively understand and deliver your requirements.
- Secure Backup and Recovery (e.g. Zerto). You are only as secure as your backups or snapshots, which provide a winner-takes-all opportunity to malicious actors. Insist your provider outlines what connects, how it connects, and how it is integrated into your total security design.
- Secure Policies & Processes. Talk to the experts and you’ll often hear the best technologies can be undermined by so-called ‘fat fingers’. We’re deeply certified with global standards such as ISO27001 and PCI that include policies and procedures as well as technologies and apps. What secures us, can secure you.
- Secure Access, Monitoring & Logging. Effective monitoring means you can meet your obligations under mandatory breach reporting legislation. It is the bedrock to securing certifications of your own to ensure best-practise Cloud security and to unlock new verticals and customers for your offerings.
Perimeter security is no longer enough. And part of a solution is no solution at all. Talk to the Macquarie Cloud Service’s team about your defence-in-depth solution today and find out why it has made them Australia’s most-recommended Colocation, Hybrid and Private Cloud provider2.
1 Gartner Australia, 2016; vForum Oct17
2 https://www.macquariecloudservices.com/blog/what-is-a-good-net-promoter-score-nps/

